In today's episode I will show you 4 little bugs in the Kallithea1 software that make it possible to access someone else's data.
Kallithea is a git server implemented in Python. So this is an alternative to GitHuba.

It also supports a less known version control system - Mercurial.
Without further ado - let's see the first error.
Users' access rights in the entire application are verified using decorators.
Every time we want to verify user's permission - we can use decorators - instead of calling HasRepoPermission.

In Python - we use @ sign for this purpose.
This solution improves code readability - now you immediately know - which method requires what permissions.
But it carries some risk.
If you do not use any decorator - the application will assume that the user has full rights to the method.
When we are looking for errors, we check all methods on the server - and make sure that the correct decorators are added everywhere.
After a few minutes of analysis - you can see that the developers have forgotten about one place2.
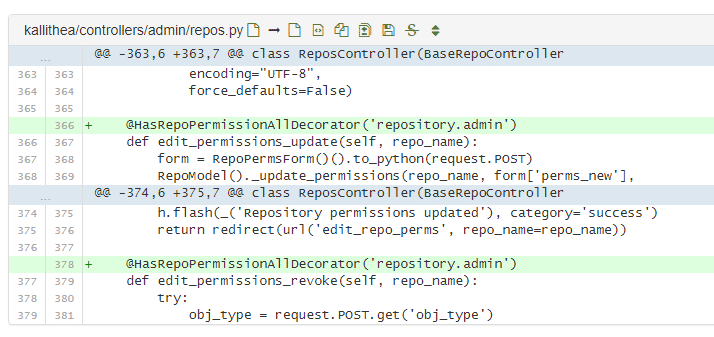
Unfortunately, this place was responsible for validating the access rights to a specific repository.
So if we know the name of someone's repository - we can add ourselves as administrators.
Thanks to this - we automatically obtain unauthorized access to code that does not belong to us.
Let's check it. I'm modifying access to the repository I own.
Then I change the name of the repository to the one I want to attack and send the request again.
I can read the contents of the secret file without any problem.

Further errors are executable only through API.
Because this server can be used not only via the web interface - certain actions can be performed also from the API level.
This is another place - that should draw the attention of the pentester.
If the application works correctly through the browser - this does not mean - that it will work properly from the API level.
This server - allows for creating repositories based on other repositories.
When creating a new repository - we can provide an address of another server from which data will be downloaded.
Thanks to this - we can easily import files from another server.
The standard usage of this functionality is to simply enter the server's http address, for example on Github.
But we are pentesters - and we try to execute a given functionality in a way that the programmer didn't expect.
The git clone function is responsible for copying data from external server. It supports http protocol, but maybe not all of you know that it allows you to enter local paths.
When we know the name of the repository - we can guess the path - where it is stored on the Kallithea server.
In a standard installation, this is the c:\kalithearepos\repository name.
All you have to do is using this path for cloning.
Then the server will automatically copy the files to which we did not have access and create our new repository based on them.
We have to do this by calling the API - because the web interface validates the cloning address.
Therefore, we need an API key - which can be downloaded from the user panel.
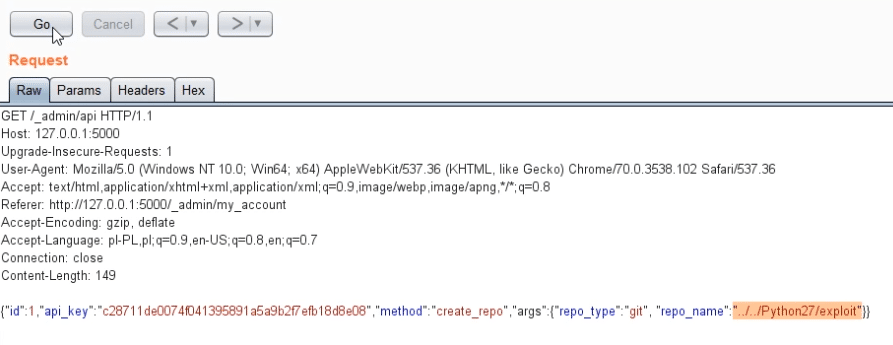
In the third error - the server did not verify if the repository name is correct if we created it via the API.
And this is important - because based on the name - the server creates a directory on the disk - in which it stores all data.
If the name contains ../ or ..\ - the system will treat it as a command to navigate to the parent directory.
This will create the repository in a wrong place that is controlled by the user.
Just like in this example, where the repository was created in the python directory, not in the repos.
Last vulnerability is also associated with the repository name.
We saw that we could specify a dot and a slash there - but the server accepted also any other ASCII character.
So it was possible to create a repository which name contained an XSS payload.
This name - is displayed in several places on the server, and this can lead to the takeover of somebody's account.
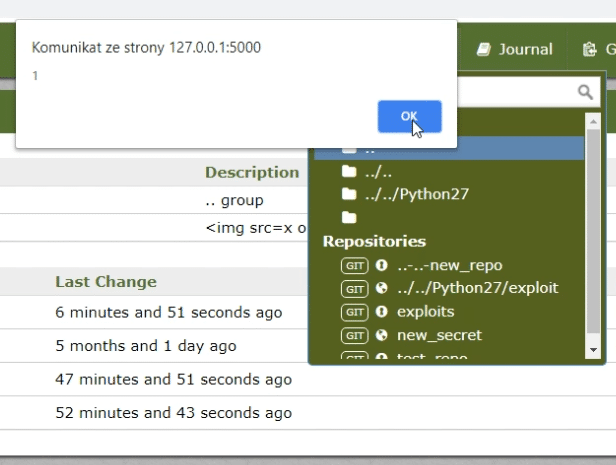
It's enough to prepare the right name - and wait until it is visited by the administrator.
Then - we can perform some actions on his behalf.
Icon made by Freepik, justicon, Iconnice from www.flaticon.com


