Today we are going to see that the platform on which we run our programs makes a difference and we'll use PHP for this purpose.
Sometimes we need to enable the user to download files from the server.
One can download all files from a specific directory except the one called secret.txt.
This functionality can be implemented in 3 lines of code.
$plik = basename((string) $_GET['plik']);
if (stristr($plik, 'sekret.txt') === false) {
echo file_get_contents($plik);
}We start with basename function, that removes all characters like ../ or ..\ from the file parameter.
Thanks to this, we are sure that the address given by the user does not contain parent directories.
Next, using the stristr function, we check if the string given by the user contains the word secret.txt.
This function contains i in its name and that means that it does not distinguish between uppercase and lowercase letters.
Therefore, we protect ourselves against the situation in which the user gave the name of our file starting with a capital letter and thus bypass the filter.
If the parameter does not have the word secret.txt in the name, the file is displayed using the file_get_contents function
Let's check how this simple script works.
In the directory I have also included the file test.txt and we'll try to display its contents first.
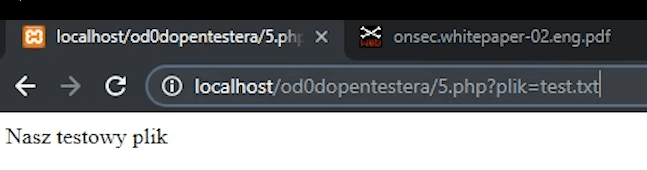
Everything works as it should. Now let's try with the file sekret.txt. As you can see, nothing is displayed.
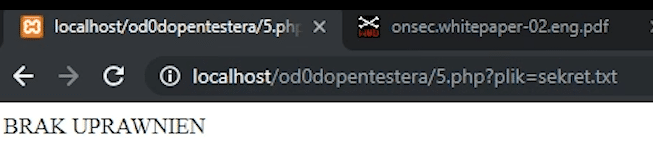
So where is the vulnerability today?
As we can read in the document entitled Oddities of PHP file access in Windows2 a string consisting of two "less-than" signs when passed to the file_get_contents function gets replaced with an asterisk.

This string is then forwarded to the FindFirstFile Windows API, that is responsible for searching for the appropriate file in the system.
There, the asterisk stands for wildcard.
So, the file that is going to be displayed is the one in which name the rest of the characters match.
So instead of passing secret.txt as the parameter to bypass the filter, we can replace the last t letter with double << sign.
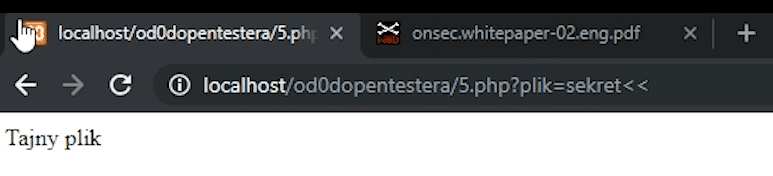
In addition to * (asterisk) we can also use:
| Character | Meaning | Example |
| " | converted into . (dot) | secret"jpg |
| > | converted ito na ? (exactly one character) | secret.jpg> |
Of course, Windows is not the most popular system used to display PHP files, what is why for most scripts this vulnerability is of marginal importance and you will never be able to use it.
However, this situation shows that such simple and popular functions as file_get_contents used to display the contents of the file may contain traces, which are not clearly described in the documentation and can be used by the attacker.


