Retrieving parameters from the user and later displaying them on the website always carries risk of XSS attack, that is - cross site scripting.
But can you perform such attack without using the html tag?
XSS happens when an unauthorized JavaScript code executes on our website.
Why is this attack dangerous? Using this code, we can steal the data of current user and perform some action on his behalf.
For example, post a post on a page or delete a photo.
When we google for XSS payloads, we can find many pages that provide a list of potential text strings used by pentesters.
It is a common practice to use the alert() function, which displays a popup with our message in the browser's window.

If with use of these payloads, we make it to display a popup, it means that we are vulnerable to this attack.
As we can see, these attacks are based on the use of HTML tags.
Tags are opened using the less-than sign and closed using the greater-than sign.
So let's take a look at today's code.
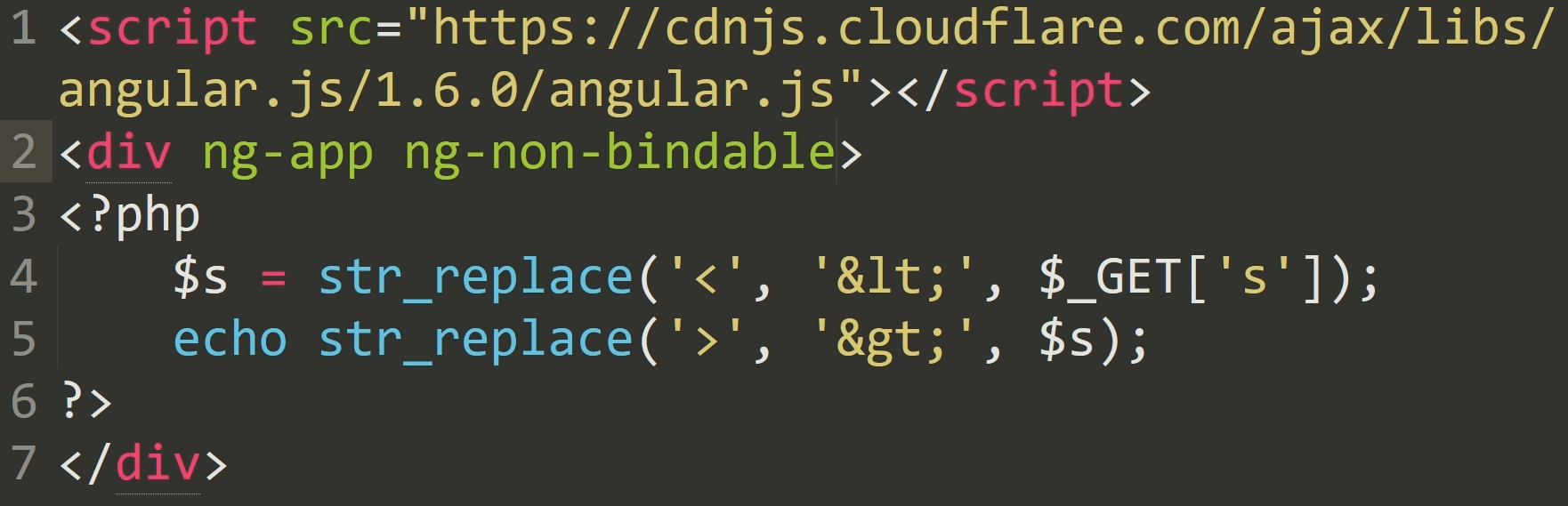
<script src="https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.6.0/angular.js"></script>
<div ng-app>
<?php
$s = str_replace('<', '<', $_GET['s']);
echo str_replace('>', '>', $s);
?>
</div>Using the str_replace1 function, we search for the < and > sings and convert them into the corresponding entities.
When the browser encounters an entity, it knows that the user does not want to open a tag, but simply display the character.
So, potentially, by replacing all such signs we should be able to protect ourselves against the XSS attack.
Let's verify this in practice - let's try to execute some payloads and see what happens.
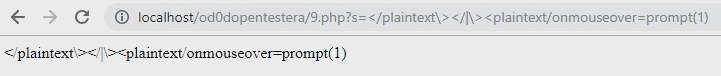
As you can see, nothing wrong happened any time.
So where is the vulnerability today?
We are going to look at the example a bit closer.
In addition to using the str_replace function, we also added an external JavaScript library named Angular2.
It is an open framework developed by Google that supports the development of Single Page Web applications
To use his goodness, I also used the div tag with the ng-app attribute.
This makes Angular know that the site uses its functionality.
So if your site uses angular - the rules of protection against XSS attacks change.
Here, like in the case of Server Side Template Injection attacks, you can use special commands - enclosed between double brackets.
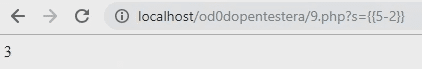
The easiest way to check if our site is vulnerable to this attack is to use math:
{{5-2}}As you can see, the subtraction result is displayed on our website.
It is time to perform some activities that are more interesting from the pentester's point of view.
Not so long ago, the angular developers tried to protect the unconscious users against such attack, by implementing the so-called sandbox.
It was supposed to filter user commands and not execute malicious ones.
However, researchers found security holes in this solution and repeatedly published new workarounds of this solution - these can be checked out on the Burp's website3.
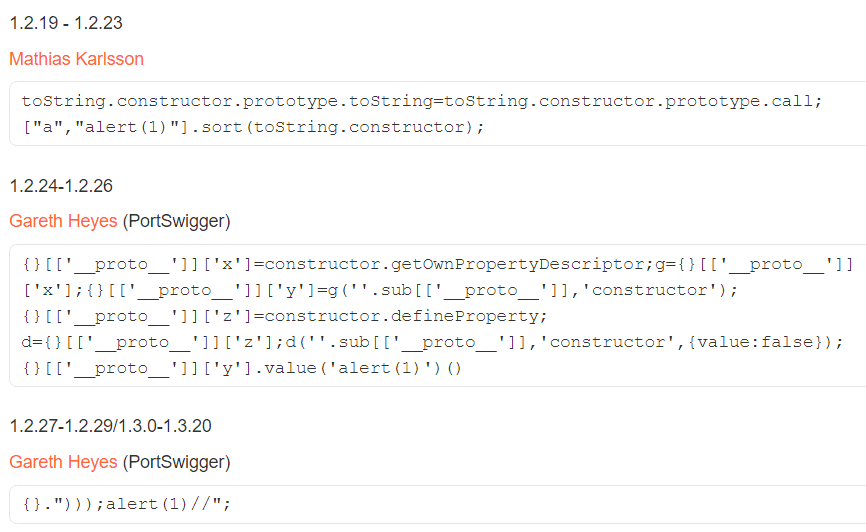
Therefore, since the release of version 1.6, the Angular's sandbox has been completely abandoned, making it easier for people searching for vulnerabilities.
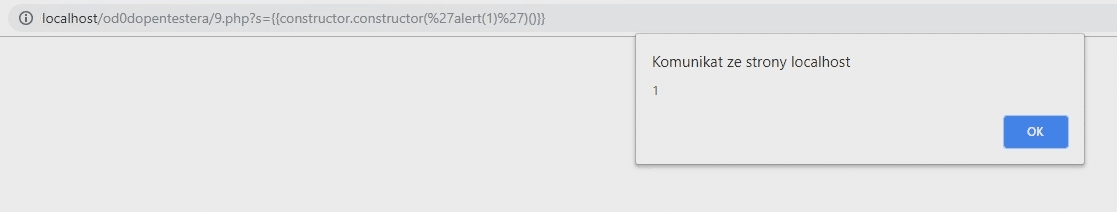
Now, instead of subtraction, we can simply use a payload - and we will see a popup with an alert message.
constructor.constructor('alert(1)')()We just executed the JavaScript code without using html tags.
The attack presented here is called Client Side Template Injection.
So how to protect yourself from this attack? In the place where the data is provided and displayed by the user, a special argument4 should be added.
ng-non-bindableSo let's add it to our div in the example script.
Now the parameter we passed is displayed as text.


