Today's episode is about functionality that can be used for phishing attacks.
It may be found on every website that allows for exporting data to CSV format.
But how the text format can be used for the attack?
Excel is a spreadsheet created by Microsoft.
It provides a large number of built-in1 functions that simplify accounting.

If we want to use a formula in a given cell instead of a number or text, we must start it with the equality sign.
Then the program knows that here the code should be executed.
For example, we can calculate the average of numbers from given cells.
In this way, you can also create a link to the external website.
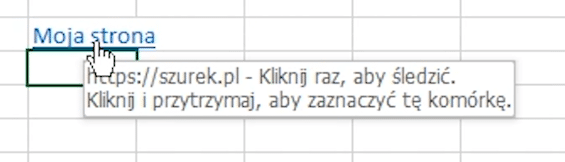
Or you can execute an external program.
This functionality is called DDE. Its syntax is very simple:
=cmd|' /C calc'!A0Microsoft realizes that this functionality can be used to execute dangerous code, so before launching it, it displays an appropriate message informing the user about potential consequences.
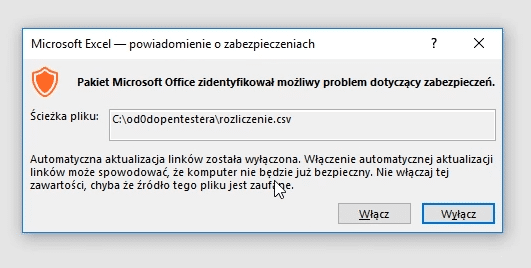
However, in reality many users keep allowing for the code execution because of habits or - ignorance.
In our case, the calculator was launched.
But how is it connect with the security of websites?
Let's assume that we are accountants and someone has sent us a link to the billing site, where we can download a list of transactions in CSV format.
CSV is a data storage format, where the values are separated by a comma.

These files can be opened by Excel - each value will be treated as a separate cell.
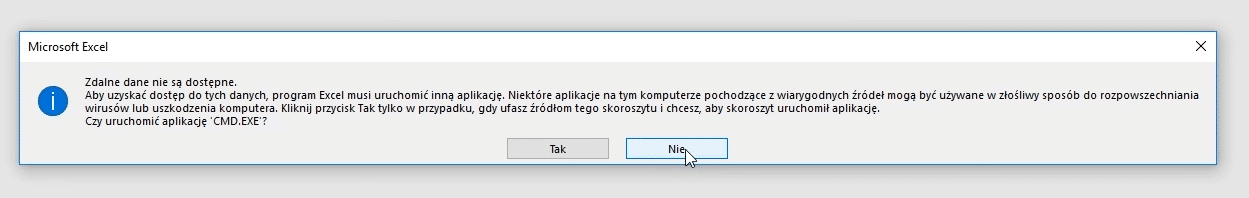
A bookkeeper may be surprised when a calculator suddenly pops up after opening a file.
If the calculator is launched, any malicious file may also be ran.
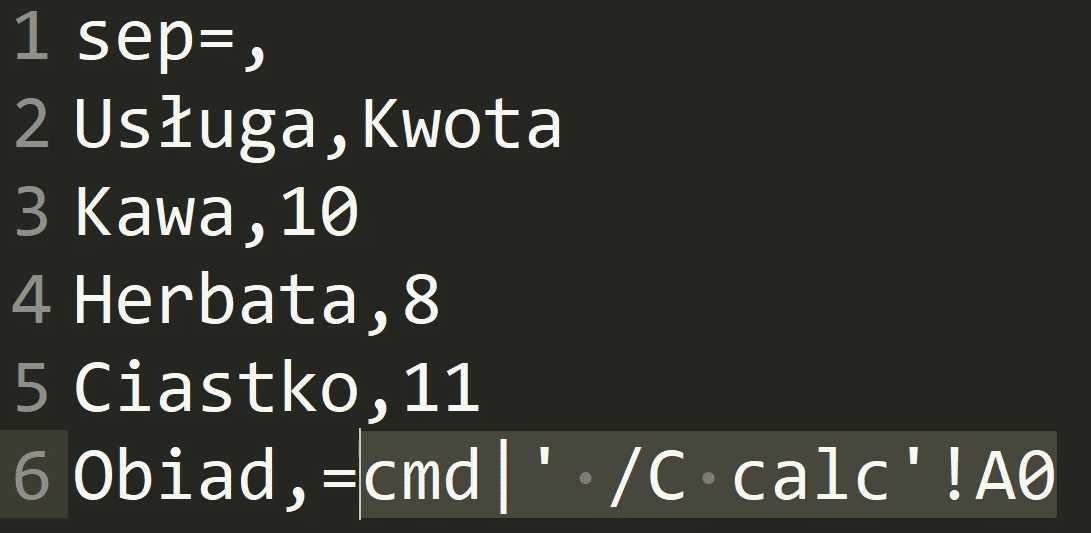
How did this happen? If file contains a value that begins with an equality sign, it will be treated as a formula and executed by Excel.
So, if we export any CSV files, it is worthwhile to precede all formulas with tabulation - they are then treated as ordinary text.
This vulnerability is called CSV Injection but most companies don't consider it to be a security hole.
For example, Google does not pay for it as part of the Bug bounty2 program.

Why? Because the user controls the content of the exported file. In addition, the attacked client must confirm whether he wants to execute additional content.
However, it is good to have knowledge about such unusual solutions. There are many potential applications that can be attacked this way.
Here, an example from the AWS console3.
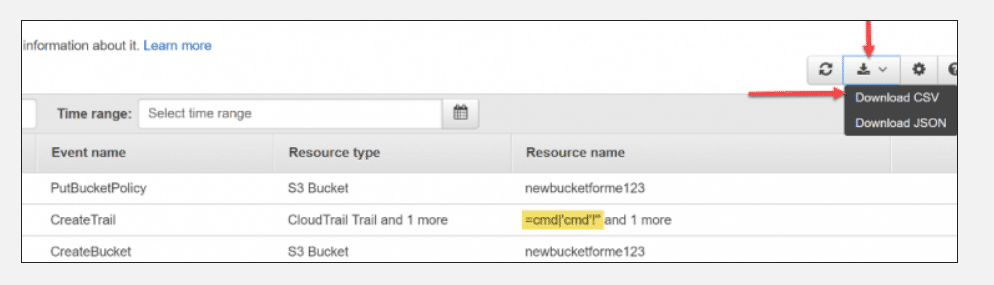
And that's all in this episode. As you can see, even a simple text format can be dangerous.


